OCR Investigators Wandah Hardy and Jeffrey Dunifon, both from Office of Civil Rights Region 5, presented today to approximately 70 representatives from Ohio Developmental Disability (DD) Boards at a special program organized by the Ohio DD Board Tech Alliance.
We will cover several of the items presented in the next few posts. Of initial interest are the most recent statistics regarding both the mechanism of breaches and the origin of breached data.
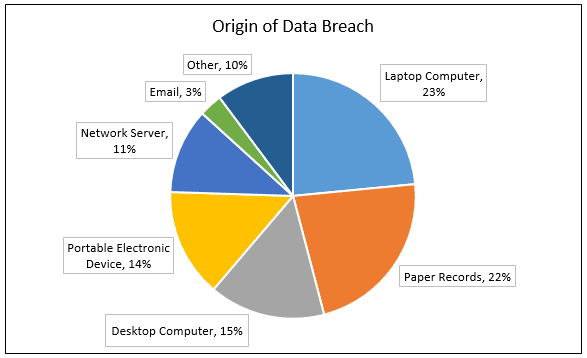 The OCR mantra for protecting against breaches is “encrypt, encrypt, encrypt.” This is because in the definition of breach, information that is encrypted, by definition, does not constitute a breach.
The OCR mantra for protecting against breaches is “encrypt, encrypt, encrypt.” This is because in the definition of breach, information that is encrypted, by definition, does not constitute a breach.
Consequently, the takeaways from these statistics include the following:
1) Encrypt all electronic data, not just portable devices. Best practice is to also encrypt desktop computers and databases containing ePHI on servers. Centrally managed encryption tools, such as Microsoft Bitlocker, become necessary and important for any but the smallest of networks. These tools allow for best practices with encryption key management.
2) Paper records account for a substantial percentage of breaches, so safeguards to protect paper records remains important. Policies should be created regarding safeguarding any records removed from the office; physical safeguards of paper records, such as locked record rooms; and careful attention to anything that is mailed out.


