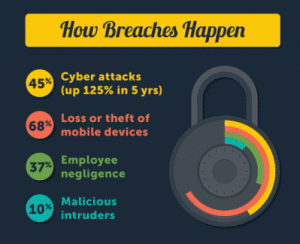
What breaches may occur when you have a Healthcare IT Vulnerability? (from a longer infographic, sourced from information at HealthIT.gov, and IDexpertsCorp.com).
As we look at healthcare IT trends for 2016, we noticed an article at Becker’s Health IT and CIO Review that made some important predictions for our hospital clients, in particular, though the cyber breaches and vulnerability issues apply also to physician groups and other provider organizations.
In a section about cybersecurity and data breaches, the authors listed concerns for the year ahead, among them the continuing “BYOD” trend. Electronic devices that operate outside your main IT system. Write’s Becker’s Max Green,
“The acronym BYOD — bring your own device — has framed the question of how to bridge patient and physician wishes for device usability while also maintaining secure hospital networks and staying HIPAA-compliant and data breach-free. Both patients and physicians have increasing expectations that when they walk into a healthcare facility their devices will be able to interoperate seamlessly with the hospital network. This can be a nightmare scenario for CIOs, with hundreds or even thousands of devices, each carrying their own respective vulnerabilities, such as malware, creating too many weak points in a network. HHS recently warned against adopting policies that allow BYOD in health systems lacking surefire means of separating private network data private and regulating employee use of devices for work duties, but the reality is that the devices are here to stay.”
Noting that often, “data breaches that result from an oversight within the network are more costly for a hospital or health system than a deliberate cyberattack” the article also observes that, “HIPAA fines for hospitals number in the hundreds of thousands of dollars, if not in the millions.” The article also covers 21 more things to know about the “state of health IT”.
HealthIT.gov has prepared several helpful PDF guides for providers, including one that covers “Breach Notification, HIPAA Enforcement, and Other Laws and Requirements”. As the guide notes, “besides HIPAA Rules, HITECH, and Meaningful Use privacy- and security-related requirements, your medical practice may also need to comply with additional privacy and security laws and requirements.”
How to guard against the increasing danger of HIPAA related breaches and avoid fines? Eagle is pleased to report that we have teamed up with Qualys, a remotely deployable, vulnerability management tool. The tool, called QualysGuard, can scan all devices on a network and identify the presence of any of 20,000 known vulnerabilities, and prepare reports highlighting issues in the order of severity.
While the use of Vulnerability Management tools such as QualysGuard are not explicitly specified as a HIPAA regulation, HIPAA does require that healthcare organizations implement measures that are appropriate to their size and scale to manage risks. For networks with 100 devices and higher, the use of an automated vulnerability management is an important risk management measure. The Qualys system is used by more than 8,000 customers in over 100 countries, including a majority of the Forbes Global 100. Contact us today for more information.
Becker’s sums up the best way to proceed by observing that solutions will come from “stronger test measures for hospital networks, such as penetrative testing software and practices, which preemptively search for weaknesses in organizations that hackers or cybercriminals could exploit. Another will be working to develop an institutional culture that places an emphasis on cybersecurity accountability, one in which staff at all levels are stakeholders in making sure the risk of a breach is minimized.”


