It was about 6PM on a Wednesday evening and I needed to do some maintenance on the EMR server. I was at home. Typically I wait until later in the evening for this kind of maintenance, but I checked and everyone was signed out of the EMR. So I signed into the server. My first clue of a problem was the error message “Missing HTML file”.
I immediately suspected a ransomware attack because the practice had been hit three times already this year. The previous attacks affected only 1 user workstation each.
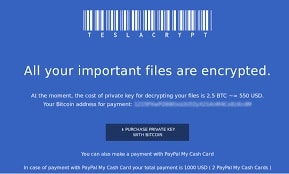
I started looking through the various folders on the server. Sure enough, the folder that the EMR uses to store scanned files and images was not in order. I recognized the pattern – many of the image files were duplicated. A new file was created with the encrypted copy, and each original file was replaced with an image displaying the message regarding how to pay the ransom. The adrenaline was surging. I could shut down this server, but which PC on the network was infected?
After shutting down the server, since I was at home and not the office, I checked to see which users were active on the network. There were three PCs powered on and active. I called each of them (I was still at home) and got a report from one of the physicians, working late at the office. He had been in his email about an hour ago and his computer slowed to a crawl. He had just opened an attachment. I told him to shut down his computer immediately.
The EMR user workstations were configured with access to the EMR image folder on the server using mapped network drives. The EMR keeps images in individual files outside of the database. Since his PC had access to this folder, the ransomware could encrypt the images. I knew the other mapped network drives, and began the process of examining each of them to see which had been damaged by the ransomware.
I came into the office, detached the PC from the network, and examined it in Safe Mode. Sure enough, its local files were encrypted also. Further review could wait until later.
My strategy was to recover everything from the backup. But just in case – if I needed to pay the ransom – I determined that I should first back up the encrypted files. Since these folders were so big, it took a while. There were many thousands of images. Finally, by 4AM, and after many Coca-Colas, this process was complete.
All backups were available online so the restoration process was relatively fast. The damaged folders were restored, and tested, by 7AM in the morning. The practice opened shortly later and didn’t miss a beat.
I was lucky. Had I not needed to maintain that server, I wouldn’t have discovered the problem until the staff returned in the morning. Even more damage would have been done. It would have certainly caused at least a full day of downtime.
Next: Post Mortem, Lessons learned, incident reporting, and corrections put into place.
See related posts on Ransomware:
Preventing and Mitigating Ransomware Attacks
2016: Hospitals targeted with Ransomware, patients harmed, losses incurred
Locky Ransomware Targets Healthcare Organizations
Ransomware Guidance from OCR

