Ransomware is a scourge, destroying computer systems, causing millions of dollars in damages, and disrupting organizations. Lately, malicious actors are using ransomware to attack hundreds of healthcare providers, businesses, and local governments. See: Premier Family Medical (Utah); NEO Urology (Ohio); ResiDex Software; Atlanta; Baltimore;
It Could Happen to You
The reality is that the likelihood of suffering a ransomware attack has never been higher. I don’t write this to be a fear-monger, but we must be aware of this sober reality and what to do about it.
Consider Three Scenarios
Picture this: You are at your computer one day when suddenly the screen blinks and this is all you see:
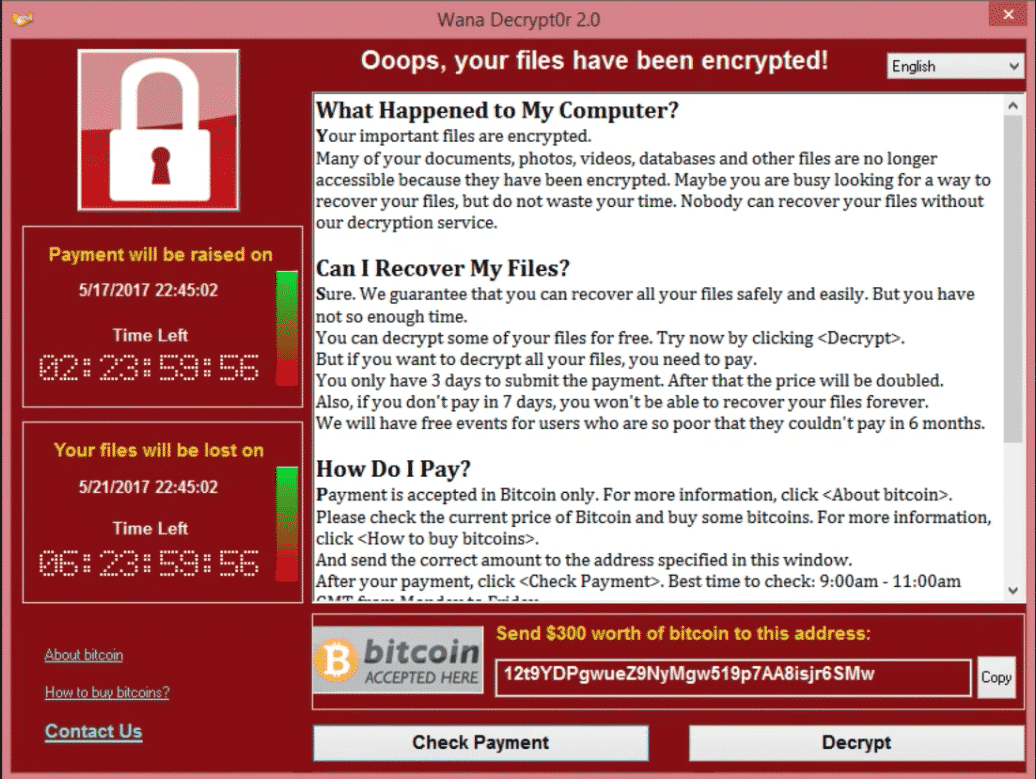
Looking around, you see your colleagues have the same screen. Quickly someone realizes the servers are also affected. Your organization is infected by ransomware. All medical records, data, systems, emails, – everything is locked up and held for ransom.
For $500,000 – or maybe $1 million – the hackers say they will give your organization the keys to unlock your systems. What do you do?
Scenario 1 – Pay the Ransom
Your organization decides to pay the ransom. What other choice do you have? The hackers own you – your primary data, your meager backups, everything. You haven’t planned for this and don’t see any other option. Like Alabama-based DCH Health System, you decide to ignore FBI recommendations and do what some infected organizations do: pay the ransom.
Maybe you get the keys to your data in return. Criminals eager to perpetuate their business may offer good customer service and promptly deliver the keys. But maybe not. Nobody said all hackers are honest. Good luck. (And even if you get the keys, the average for data return is only 92%, due most often to poor encryption).
Scenario 2 – Attempt Restoration
Your organization refuses to pay the ransom. Good for you, in theory. Unfortunately, just like in the previous scenario, your organization isn’t actually prepared for this situation. You hire outside consultants and ransomware decryption specialists, buy more computers and servers, and piece-by-piece try to restore your data. It takes days, weeks, or months of work and a lot more money than the ransom would have cost, and in the end, you still aren’t guaranteed to be back at 100%. But most importantly, with every day that goes by, your organization’s reputation crumbles, you lose customers and revenue (thousands or tens-of-thousands of dollars per day).
A ransomware attack or other disaster could put you out of business.
Consider this:
According to a report on ransomware by Coveware, “downtime costs are typically 5-10x the actual ransom amount and are measured in lost productivity (slack labor and lost revenue opportunities).”
Scenario 3 – Implement your thoroughly-tested Disaster Recovery Plan
Same infection, same ransomware. This time, you call your IT support team. They sigh resignedly, bracing themselves to work overnight for a few days, maybe to work all weekend. Then they pick up your organization’s Disaster Recovery Plan, assess the situation, and get to work. It is a rough few days. Operations are stuck without the IT systems.
But a few days later, everything is back up and running. Maybe a day’s worth of revenue was lost, but that’s about it. Total cost is a few thousand dollars in overtime (the IT support team) and lost productivity (everyone else).
Which scenario do you want to go through?
Disaster Recovery Planning Makes A Difference
The organization in scenario 3 could recover so quickly and (relatively) painlessly because they had prepared a Disaster Recovery Plan before the disaster struck.
A Disaster Recovery Plan (DR Plan) is a written, detailed, and tested plan that specifies the actions an organization will take prior to a disaster and the actions during and after the disaster to recover quickly. For this article, we will focus the DR Plan on restoring the IT capabilities and critical electronic information of an organization.
In brief, preparing a DR Plan involves the following process:
- Establishing the planning team of management, stakeholders, and experts.
- Documenting the computer network(s) and critical systems, assets, and data sets.
- Identifying possible disaster scenarios and their likelihood of occurring. This should include everything from hardware failure to a ransomware attack to a tornado destroying the data center.
- Establishing recovery priorities, including the organization’s expectations for how quickly systems should be restored (called a Recovery Time Objective, or RTO) and how much data from before the disaster the organization is willing to lose (called a Recovery Point Objective, or RPO, which informs the frequency of backups). This usually involves some negotiation, because improvements in RTO and RPO cost money.
- Developing strategies for prevention, mitigation, and recovery in order to meet the priorities from above.
- Implementing those strategies.
- Detailing everything in a written plan, which is then disseminated in digital and hard copy to key stakeholders.
- Testing the DR Plan to make sure it will work during a real disaster. The plan isn’t done until it is tested. Testing validates that all key steps are included and that recovery can be done. Testing finds the gaps, the missed steps, and fixes them.
Create a Disaster Recovery Plan for Your Organization
If the worst happens, does your organization have a DR Plan ready? Is that plan detailed, written, and regularly tested? If not, start working on one today, so you do not risk potentially catastrophic damages or going out of business from a cyberattack.
Eagle Consulting Partners has experience preparing DR Plans for healthcare organizations, businesses, and government agencies. We can lead your team through the process, too. Contact us today for expert help preparing a Disaster Recovery Plan for your organization.

