OWASP Top 10 from owasp.org
Molina Healthcare, a leading Medicaid and Affordable Care Act insurer across 12 states, recently suffered a security breach in which patient records were exposed on their online subscriber portal. The application flaw, which was present on the web for nearly a month before it was corrected, allowed patients to view claims and other sensitive information, such as names, address, diagnosis, and other medical information, of other Molina patients without any authentication restrictions. Molina was informed of the flaw by web security blogger Brian Krebs.
In a statement, Molina officials confirmed that they are now “conducting an internal investigation to determine the impact [the breach has had], if any, to [their] customers’ information.”
In order to effectively protect from online security breaches, it is important to understand the issues in deploying online web applications, as their exposure to the internet puts them at a higher risk for hacking. It is essential to address web security when developing online apps. A few key ways to ensure security and confidentiality for organizations who deploy online applications include:
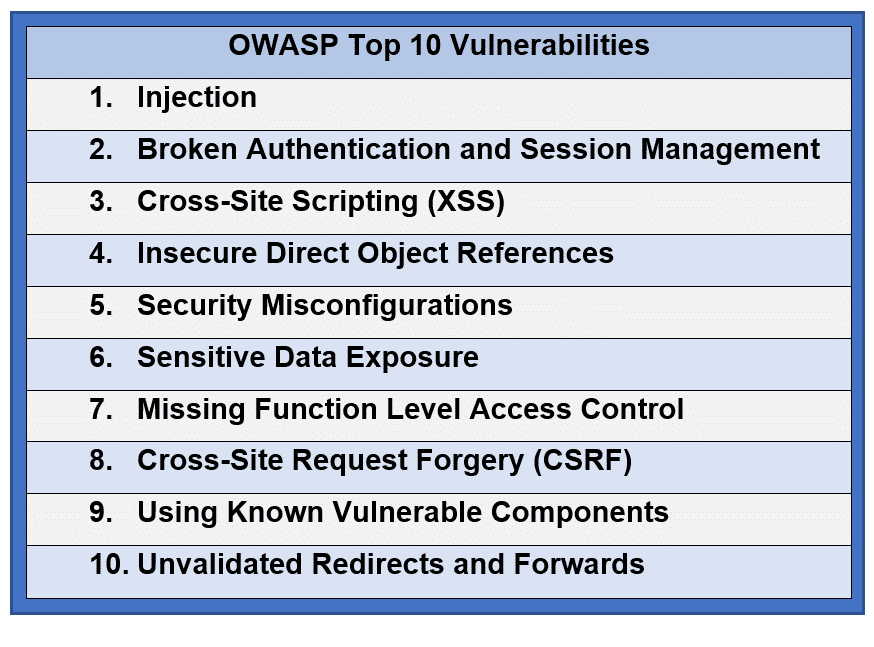
- For organizations who develop their own applications, a good start to web security is ensuring that applications exclude any vulnerability outlined in the OWASP Top 10 Application Security Risks. A rigorous tool to validate that these vulnerabilities are not present is the OWASP Testing Guide. In addition to internal testing, third party reviews and/or penetration testing will enhance the security posture.
- In order for programmers to build secure applications, they need to understand secure programming techniques. Programmer Security training and competency testing is an important control. Training should be specific to the environment in which they are programming. One resource for platform-specific programmer training is the vendor Security Innovation.
- Security of purchased applications. It is not prudent to assume that vendors create secure applications. Part of due diligence in acquiring applications is requiring evidence of good security. Vendors can be asked to provide 3rd party verification of security, such as penetration test results. Another protection is to require a Business Associate Agreement that includes indemnification in the event of a data breach, and to require that the vendor maintain an appropriate amount of data breach insurance in the event of an incident.

