Hospitals, physician practices, government agencies, business associates and others who must comply with the HIPAA Security regulations should dust off the previous HIPAA Security Risk Analysis and update it for 2011. Hospitals and Physician practices qualifying for meaningful use incentive payments have a great motivation already. But even if you are not in line for these government incentive payments, you should take this step. This is because your anti-virus protection – no matter which vendor you use – is broken.
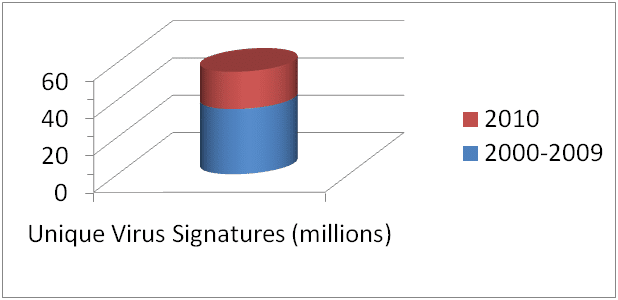
- In 2010 the Number of Viruses Skyrocketed 70%, a growth of 20 million
Traditional virus protection, or anti-malware software, uses on a unique “virus signature” to identify a specific virus. The virus is studied, removal methods are developed, and both cataloged in a database. There are multiple problems. First, the number of unique viruses exploded in 2010, with 20 million new viruses found, a 70% increase in the cumulative total, which has overwhelmed traditional methods. Second, virus writers have learned to evade detection by creating many variations, and other techniques, so that traditional detection methods are thwarted. Countermeasures, such as “heuristic” techniques used by anti-malware writers, are ineffective in detecting all of these new viruses.
Compounding the dramatic increase in malicious software is an alarming rise in defects in popular programs. Just what is vulnerable? The most common targets are programs on the individual user workstations. According to recently released research from security firm Secunia, the median user has 66 programs installed on their computer from 22 different vendors. Using as an example a user with the Top 50 Programs installed, 26 are provided by Microsoft and 24 by 14 other vendors. During calendar year 2010, number of vulnerabilities in these 50 programs increased from 426 to 729, a 71% increase. Almost all of this increase came not from Microsoft programs, but from the 14 other vendors.
You may ask who is behind all of this malware. Most of the growth is a partnership between nefarious technical experts who create “attack kits” – software that empowers a criminal (or groups of criminals) of lesser technical expertise to create their own cybercrime enterprise. The motivations include online banking theft, blackmail, theft of trade secrets, identify theft, ATM theft, on-line fraud such as sale of bogus anti-virus software, corporate espionage, and political activity. Be particularly careful about your own online banking!
The appropriate countermeasure is to update, or “patch” the vulnerable programs on your computers. These include popular titles like Adobe Acrobat Reader, Adobe Flash Player, Apple ITunes, RealPlayer, Google Picasa, Apple QuickTime, Mozilla Firefox, Google Chrome, Apple Safari, etc. When the program is updated, or “patched”, the vulnerability is eliminated and you will not be harmed by malware which attempts to exploit this vulnerability. Unfortunately, it is not easy update all of this software on a timely basis on one computer – much less on all the computers in your organization. Home users may benefit from the free Personal Software Inspector (PSI) from Secunia to help with this task. Stay tuned in for future posts that deal with practical solutions for organizations.
Editor’s Note: Subsequent to the publication of this article, CMS has renamed the “Meaningful Use” programs and MIPS “Advancing Care Information” category to “Promoting Interoperability”.

