Incidents of cyber-espionage have shown consistent, significant growth and display a wider variety of threat actions than any other pattern discovered in Verizon’s recent 2014 Data Breach Investigations Report, which analyzed of over 63,000 confirmed security incidents which collected data from 50 contributing organizations across 93 countries.
While cyber-espionage is a very significant threat –only a very small percentage of confirmed cyber-espionage incidents – less than 1% — involved healthcare organizations. Our assessment is that the most likely organizations to be at risk are large, sophisticated hospital systems active with research and product commercialization activities with valuable intellectual property.
Of the 511 total incidents reported by survey respondents, 59.88% had confirmed data disclosure. Verizon notes that the most evident change from their last report includes “the rise of strategic web compromises and the broader geographic regions represented by both victims and actors.” There was also a wide distribution of both sizes and types of victim organizations, indicating that size doesn’t seem to be a significant targeting factor.
Other key findings include:
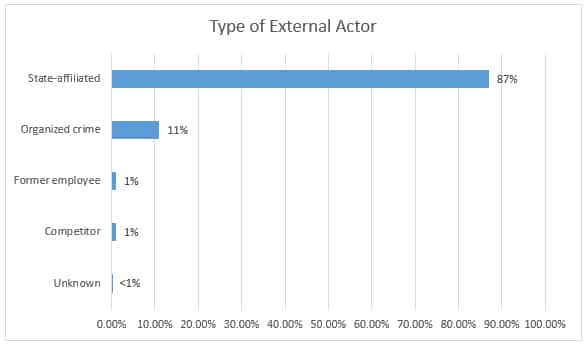
- A significantly high percentage—87%–of the cyber espionage incidents analyzed were affiliated to state-affiliated actors. See the breakdown by type of external actor here:
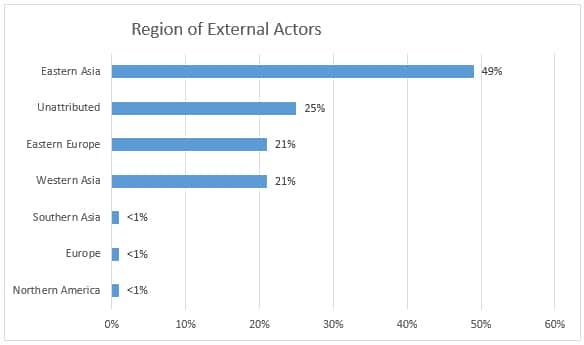
In terms of the nation states responsible, China and North Korea (categorized together as North Asia) are definitely not the only countries conducting espionage. The 2013 data reflected an increase of activity attributed to Eastern European actors.
- While the specific threat actions involved don’t come as a huge surprise, what’s surprising is the wide variety of threat actions. Take a closer look at the types below (Incidents of hacking and malware were tracked separately and incidents often had more than one type of threat action.):
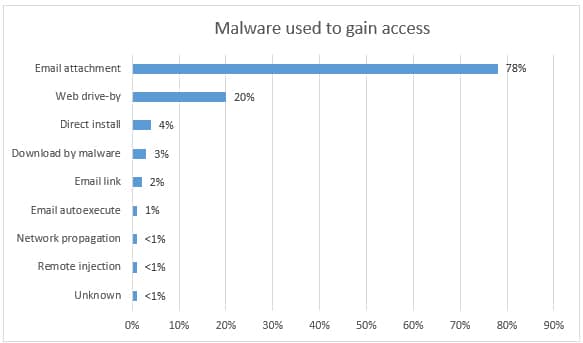
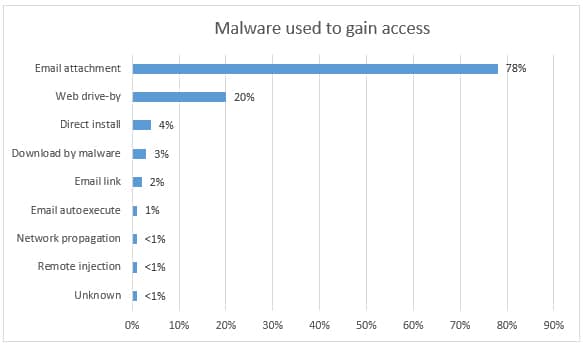
- The methods of gaining access reported were not as diverse as the tools used.
- Phishing emails still top the list at 78%, a decrease from the prior year’s percentage of 95%.
- Verizon notes that strategic web compromises as an access method increased significantly to 20%. This method uses websites that target mostly by demographic. When visitors hit the site, the trap is spring, the system infected, and the malware is installed on the system that opens a backdoor or command channel, allowing the attacker to initiate their objectives
See the chart below for the breakdown:
Verizon and Eagle Consulting Partners recommend the following action steps to combat against cyber espionage at your organization:
- Patch your browser, operating system and other third-party software regularly.
- Use (and update) appropriate anti-virus, mainly to detect anomalies in applications and find pesky malware
- Train users, making sure they know how to recognize and respond to incidents quickly
- Segment your network to contain incidents
- Keep good logs of system, network and application activity
- Defend against phishing by considering employee security awareness training.
- Stop lateral movement inside the network with two-factor authentication, network segmentation and watching for user behavior abnormalities stemming from compromised accounts for behavioral.
The annual release of the Verizon Data Breach Investigations report is extremely useful for the risk analysis process. Eagle’s standard computer security risk analysis practice includes a thorough review of your organization’s current security practices and provides estimates of risk based on real-world data including the findings of this important industry study. Further, our corrective action recommendations in these risk analysis studies will usually include the best practices cited above along with other relevant industry-standard practices. You can learn more about Eagle’s risk analysis for hospitals or medical practices here.