According to research published by security organization FireEye Labs, massive email campaigns were identified during August 2016 distributing the Locky ransomware. While the spam was distributed worldwide and across various industries, the U.S. received the highest numbers, and healthcare received 10 times the quantity of emails as the next highest. So clearly the healthcare industry is being targeted. Here are the statistics, courtesy of FireEye:
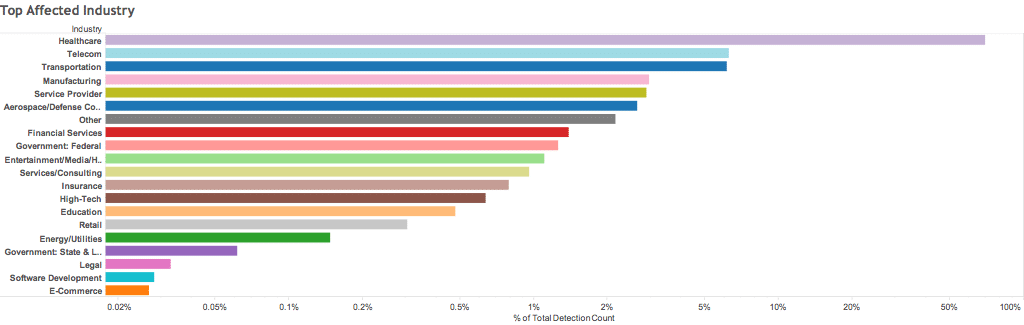
Industries affected by massive spam campaign to distribute Locky ransomware, during August 2016, courtesy of security firm FireEye
Note that the chart has a logarithmic scale, and that the healthcare industry received more than 50% of the entire spam campaign. So clearly, healthcare is being targeted by this criminal gang.
While the Locky ransomware has been delivered via spam during the course of 2016, from campaign to campaign the specific tactics are constantly changing. During August, the spam offered the victim an attached Microsoft Word .DOCM file (a Microsoft Word file containing a macro) showing an invoice. Earlier in the year, FireEye observed that the the email included an attached javascript downloader.
Takeaways for healthcare organizations are that healthcare organizations are at greater risk for this type of malware, that email is the preferred delivery vehicle, and that the specifics of the campaigns are continually evolving.
Countermeasures include tightly configured spam filters on email systems, group policy which disables macros in Microsoft Office, and security awareness training. However, since the specific delivery tactics are continually evolving, please see Preventing and Mitigating Ransomware Attacks for a more comprehensive list of preventative and mitigating countermeasures.

