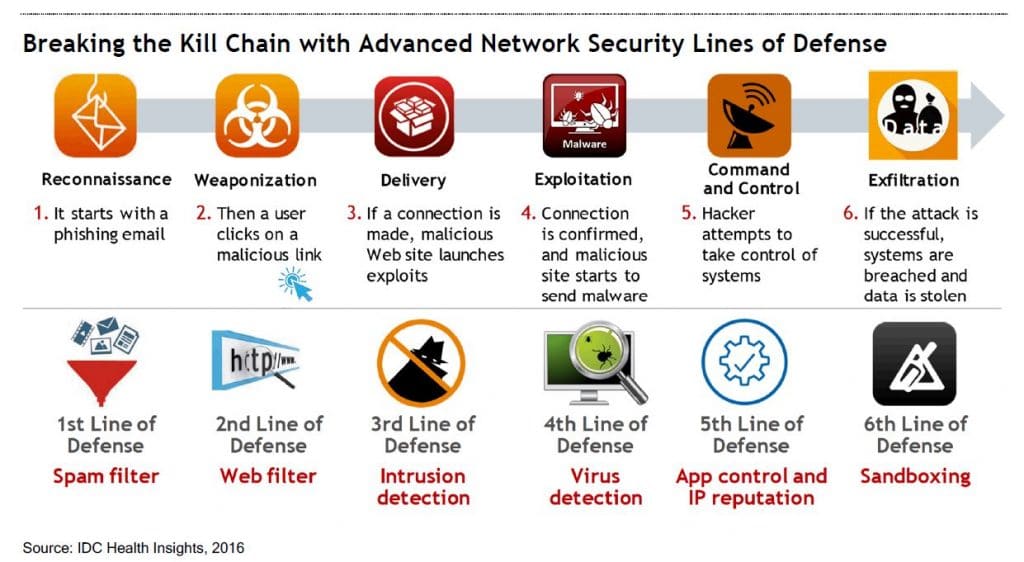
What can you do to stop ransomware attacks at hospitals? An accurate risk analysis is the key.
First up are measures that can prevent the infection in the first place:
Preventative Measures
- Security Awareness Training. One of the most common “attack vectors” for the ransomware attacks are infections via “phishing” emails, followed by malware delivered from infected websites that end-users may visit. No technical solution is fool-proof. Consequently, educating end users about ransomware, how to recognize potentially dangerous emails and other risks, and what to do in the event of an infection is a vital safeguard.
- Tighten Firewall Rules. The firewall provides powerful features that can provide protections. These include restricting or preventing traffic from foreign locations, incorporating whitelists and/or blacklists, and paying attention to other best practices can help.
- Patching. In many cases, ransomware relies on the presence of unpatched, unsecure software in order to infect a machine. The most common “attack vectors” are unpatched versions of Adobe Reader, Adobe Flash, Java and the browsers Internet Explorer, Chrome and Firefox. While there are many other operating, application and network device software programs that should be included, we recommend prioritizing the above. Another strategy is to use an alternative PDF reader such as Nitro and eliminate Adobe Reader altogether.
- Secure Configurations. Organizations should be using configuration guides to securely configure the operating system, network gear, and application programs. In particular, one significant attack vector is malware spread through Microsoft Office file macros. By disabling automatic running of macros in Microsoft Word and Microsoft Excel, infections can be prevented.
- Ban Personal Webmail. Since email is a known attack vector, organizations can prohibit employees from accessing their personal email from the corporate network. Most people can access their email from phones so this will not create a major hardship. This can be enforced with firewall rules.
- Network Protection Tools – Intrusion Detection and Prevention Systems, Advanced Persistent Threat detection tools and other tools can identify and prevent malware from infecting your network and/or can provide you early warning so that you can launch mitigation efforts.
- Email Filter. Invest in tools for email filtering to scrub email from malicious attachments and malicious links.
- Anti-malware Tools. Keep anti-virus/anti-malware tools up to date and operational.
- Threat Intelligence. Invest in threat intelligence so that you can prepare in advance for likely attacks. By knowing what strains of ransomware are spreading and which attack vectors are used, highly specific countermeasures can be put into place to prevent and/or mitigate a ransomware attack.
Even the network with the best protections will find itself with a piece of ransomware that has infected a device. Since that is the reality, we offer a second list of measures, which are equally or even more important, that will reduce the impact of the infection, contain the malware, and assist with eradication and restore any data that was corrupted. Our Mitigation Measures:
Mitigation Measures
- Robust Data Backup & Recovery Capability. In the event that you are hit with ransomware, your “Ace in the Hole” is a robust Data Backup and Recovery capability. Here are some characteristics of the capability:
- Data Criticality Analysis – Make sure you carefully review your important data so you don’t miss something with your backup. Don’t forget cloud data!
- Multiple Backup Generations – Since you won’t necessarily discover ransomware immediately, make sure that you have multiple generations of backup. At least 10 generations covering a minimum of the previous 2 weeks are recommended.
- Isolate Backup – Don’t leave your backup on the network to be encrypted! Send the backup off-site to a totally separate network, or use removable media.
- Redundant Backups – Keep multiple backups. Consider using multiple tools for these backups.
- Recovery Capability – Invest in training and other tools to be able to perform rapid recovery of servers, workstations and other devices. Use virtualization technology whenever possible. Perform trial recoveries on a regular basis.
- Network Segmentation – Segment the network using VLAN and other technologies to prevent the spread of ransomware that may find its way into the network.
- Permissions Management – Use the principle of least privilege to remove administrative rights from end-users and to limit the write permissions to network drives.
- Regular Vulnerability Scanning – Regular vulnerability scans can assist both as a preventative and mitigation measure. The scans can detect unpatched software, which when patched can prevent malware spread. The scans can also identify configuration issues which would permit a more rapid spreading of ransomware through the network.
- Incident Management – Even the best organizations will experience some penetration of their network. By investing in incident management capability, you will be able to rapidly respond first to contain ransomware, to rapidly eradicate it, and finally to restore any corrupted data from the backups.
None of these measures are new concepts. However, few organizations have all of the human and financial resources that they would like for their security program. In order to implement all of these measures, top management may need to allocate more budget in order to protect the organization. To justify the expenses, it is important to prepare a thorough and accurate risk analysis which quantifies for top management the potential impact of ransomware and the likelihood of it occurring. Only with this information can top management make the trade-offs necessary to make the wisest investment decisions.