IT Risk Management Services

Risk management begins where a security risk assessment leaves off. Eagle assists organizations with maturation of their risk management approach and helps comply with regulatory obligations such as HIPAA, CMMC or SOX.
Eagle’s Security Risk Management support services assist clients after delivery of security risk assessment. An effective security risk assessment can include a handful of major risks and ten, twenty or more minor risks, along with dozens of recommendations to treat these risks. The risk management process is ongoing and never ending. This can be overwehlming, and most organizations conduct risk management using an informal process at best.
Certain regulatory frameworks, such as the HIPAA regulations, mandate that organizations implement a formal risk management process. Through this process, organizations must “implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with the HIPAA Security Rule.” The regulation further mandates that formal documentation of the risk management process be maintained.
Eagle support services will help the organization mature and formalize its risk management process. Eagle guides CISOs and other security officials with an effective process to ensure that the proper management staff are involved, and that risk acceptance decisions be made at the appropriate level, and that proper documentation of these decisions is maintained. In addition, Eagle can help prioritize what could be a myriad of corrective action recommendations, such as:
- Implementing encryption of mobile devices, workstations and databases
- Selecting and implementing a secure email solution
- Updating custom applications to include appropriate access controls and audit trails
- Auditing vendors and contractors
- Creating an internal audit program to monitor employee use of electronic record software
- Conducting a technical vulnerability analysis and/or penetration test of the computer network
- Updating formal security policies
- Implementing an effective employee training program, including initial training and ongoing security awareness training
- Upgrading the system backup and conducting recovery testing
- Implementing a System Information and Event Monitoring System and/or audit log monitoring system
- Implementing a mobile device management system
For organizations who take compliance seriously, the list of projects can be overwhelming. Simply achieving basic compliance often requires a multi-year effort. Eagle provides Risk Management support, including both project management and/or project support for any of the above projects.
We work with your team to create a project plan that prioritizes projects based on overall security risk reduction. Next, we regularly meet with both management and appropriate staff members to implement the plan. Eagle Consulting adds value by driving the Risk Management effort, using best-practice processes and creating the documentation which which may be required in various regulatory frameworks such as HIPAA or SOX.
In addition to project management, we can assist with completing specific Risk Management projects. Examples include, but are not limited to, providing staff training, managing the ongoing security awareness training program, conducting a technical vulnerability analysis, or conducting a penetration test.
Let Eagle’s Risk Management Support services give you peace of mind knowing that your organization is being guided toward risk management compliance.
Call us today at 216-503-0333, or fill out the form below and someone will be in touch with you.
Recent Related Posts
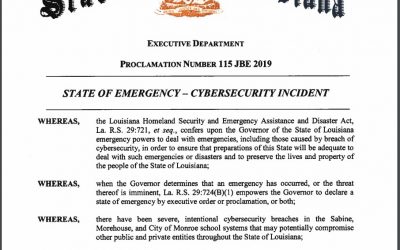
Ransomware Causes Delay in Start of School Year and State of Emergency Declaration
Targeted ransomware attacks hit 4 Louisiana school districts, causing the governor to declare a State of Emergency.
PSA: Ransomware Outbreak Insights from CISA
The DHS Cybersecurity and Infrastructure Security Agency (CISA) just issued a special publication about ransomware protection and recovery. Read it here.
Sell More to Hospitals with a HITRUST Certification
The Provider Third Party Risk Management Council, made of a consortium of leading hospitals, introduced a new approach to third-party risk management. How can you better serve them? The solution is simple – any vendor of a certain size who wishes to do business with one the member hospitals must successfully complete – and annually maintain — a certification using the HITRUST CSF. Member hospitals will accept a HITRUST certification as evidence of a robust security program. No questionnaires or further dialog is necessary.